A cryptocurrency mining campaign targeting macOS is using malware that has evolved into a complex variant giving researchers a lot of trouble analyzing it.
The malware is tracked as OSAMiner and has been in the wild since at least 2015. Yet, analyzing it is difficult because payloads are exported as run-only AppleScript files, which makes decompiling them into source code a tall order.
Malware Analysis Tool For Mac Os

- MacOS Malware Analysis Tools Static Analysis. JTool – A better variation of otool. What’s your Sign – Checks code-signing certification status. Dynamic Analysis. ProcessMonitor – Monitors processes activities. FileMonitor – Monitors file system events. Reverse Engineering.
- KnockKnock uncovers persistently installed software in order to generically reveal malware. TaskExplorer allows one to visually explore all running tasks (processes). Quickly see a task's signature status, loaded dylibs, open files, network connection, and much more.
Volume 0x1: Analysis Starting with introductory topics such as infection vectors, persistence mechanisms, and payloads, this content-packed volume also covers in detail, the tools & techniques needed to comprehensively analyze malware targeting Apple's desktop OS. And here’s the good news: you actually now have all the tools installed that you need to learn macOS malware analysis and reverse engineering! These tools include a string decoder ( strings ), file analysis utilities ( file, nm, xattr, mdls and others), hex editors ( hexdump, od, xxd ), a static disassembler ( otool ), and a debugger, memory reader and dynamic disassembler ( lldb ). Cuckoo Sandbox is an advanced, extremely modular, and 100% open source automated malware analysis system with infinite application opportunities. By default it is able to: Analyze many different malicious files (executables, office documents, pdf files, emails, etc) as well as malicious websites under Windows, Linux, macOS, and Android.
A recently observed variant makes analyzing even more difficult as it embeds a run-only AppleScript into another scripts and uses URLs in public web pages to download the actual Monero miner.
Reversing run-only AppleScript
OSAMiner typically spreads via pirated copies of games and software, League of Legends and Microsoft Office for macOS being among the more popular examples.
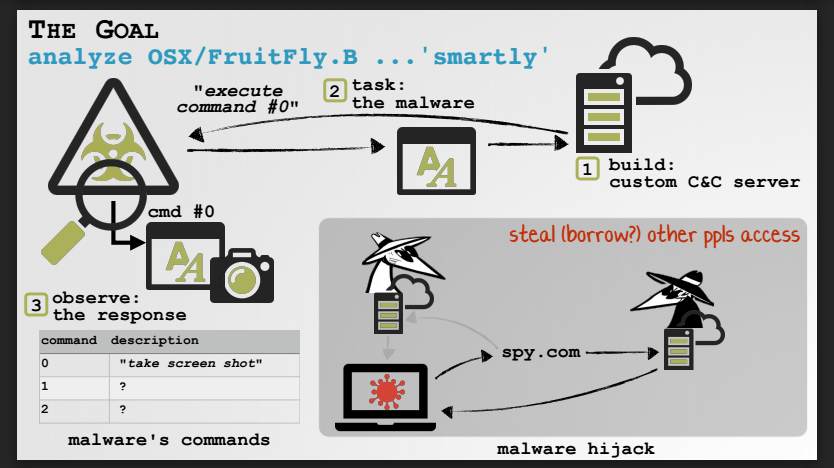
The malware has been researched in the past [1, 2] but the run-only AppleScript file hindered full analysis, limiting it to observing the behavior of the sample.
AppleScript files include both the source and the compiled code but enabling 'run-only' saves only the compiled version so the human-readable code is no longer available, thus removing the possibility of reverse engineering.
Security researchers at SentinelOne discovered at the end of 2020 a new sample of OSAMiner that complicated 'the already difficult process of analysis.'
However, they were able to reverse engineer some samples they collected by using a less-known AppleScript disassembler (Jinmo’s applescript-disassembler) and a decompiler tool developed internally called aevt_decompile.
Evasion actions
The recent OSAMiner campaigns use three run-only AppleScript files to deploy the mining process on the infected macOS machine, SentinelOne found:
- a parent script that executes from the trojanized application
- an embedded script
- the miner setup AppleScript
The main role of the parent script is to write the embedded AppleScript to ~/Library/k.plist using a 'do shell script' command and execute it. It also checks if the machine has enough free space and exits if there isn't sufficient storage.
Other tasks it runs include collecting the serial number of the device, restarting the 'launchctl' job responsible for loading and unloading daemons or agents, and to kill the Terminal application.
The researchers say that the main script also sets up a persistence agent and downloads the first stage of the miner from a URL set on a public page.
Some samples may not lead to a live URL. However, SentinelOne was able to find an active one (https://www[.]emoneyspace[.]com/wodaywo) and noticed that the malware parsed a link in the source code of the page that pointed to a PNG image.
This was the third run-only AppleScript, downloaded to the ~/Library/11.PNG. Its purpose is to download the open-source XMR-Stak Monero miner that works on Linux, Windows, and macOS.
'The setup script includes pool address, password and other configuration information but no wallet address,' the researchers say in a report today, adding that it also uses the 'caffeinate' tool to prevent the machine from entering sleep mode.
Evading detection
According to SentinelOne, the second script is intended to prevent analysis and evade detection. Supporting this conclusion is killing the Activity Monitor, which is the equivalent of the Task Manager in Windows, likely to prevent users from checking the system's resource usage.
Furthermore, the script is designed to kill processes belonging to popular tools for system monitoring and cleaning. It finds them by checking a hardcoded list.

SentinelOne says that while AppleScript incorporates more powerful features [1, 2], the authors of OSAMiner are not currently taking advantage. This is likely because the current setup allowed them to run their cryptocurrency mining campaigns with little resistance from the security community.
However, as SentinelOne proved, the technique is not infallible and researchers have the means to analyze it and prepare defenses against other malware that may choose to use it.
Related Articles:
These books are peer-reviewed and open to community input. Moreover the digital versions are 100% free!

...look for printed copies later this year!
- Volume 0x1: Analysis
Starting with introductory topics such as infection vectors, persistence mechanisms, and payloads, this content-packed volume also covers in detail, the tools & techniques needed to comprehensively analyze malware targeting Apple's desktop OS.
📖 Read Online/ 📥 Download PDFs
Malware Analysis Tool For Mac Shortcut
Patrick Wardle is the founder of the 'Objective by the Sea' macOS security conference and the creator of the macOS security website & tool suite Objective-See.Having worked at NASA and the NSA, as well as presented at countless security conferences, he is intimately familiar with aliens, spies, and talking nerdy. Patrick is passionate about all things related to macOS security and thus spends his days finding Apple 0days, analyzing macOS malware and writing free open-source security tools to protect Mac users.
The 'Art of Mac Malware' was created to provide a comprehensive resource about threats targeting Apple's desktop OS. Dedicated to the community, it is a culmination of over a decade of macOS security research!
But, I need you help! As you're reading the books online, you are encouraged to provide feedback if:
- You notice a grammar or spelling error.
- You spot a technical error or inaccuracy.
- A topic is confusing, inadequately covered, or could be improved by the addition of an external resource.
Also, if you're stoked on the goals of this project and want to support my efforts (and gain early access to new chapters!)
...join me on patreon: